Many people use virtual private networks (VPNs) to increase the privacy and security of their Internet browsing, as well as to access content outside of their region. For most people, this means you get a completely secure connection with no ability for corporations or governments to spy on you – but that’s apparently not the case for iOS users.
The issue, uncovered by security researcher Michael Horowitz, is this – typically, when a VPN connection (officially known as a “tunnel”) is made, all existing connections are terminated and reestablished inside this tunnel. But Horowitz says this doesn’t happen with iOS devices, such as an iPhone or iPad.
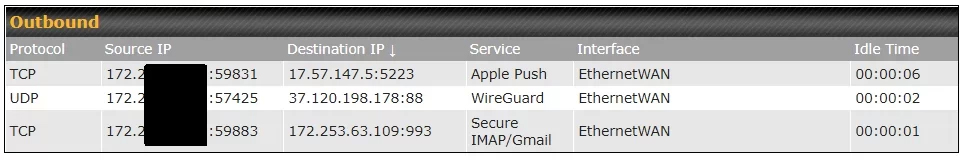
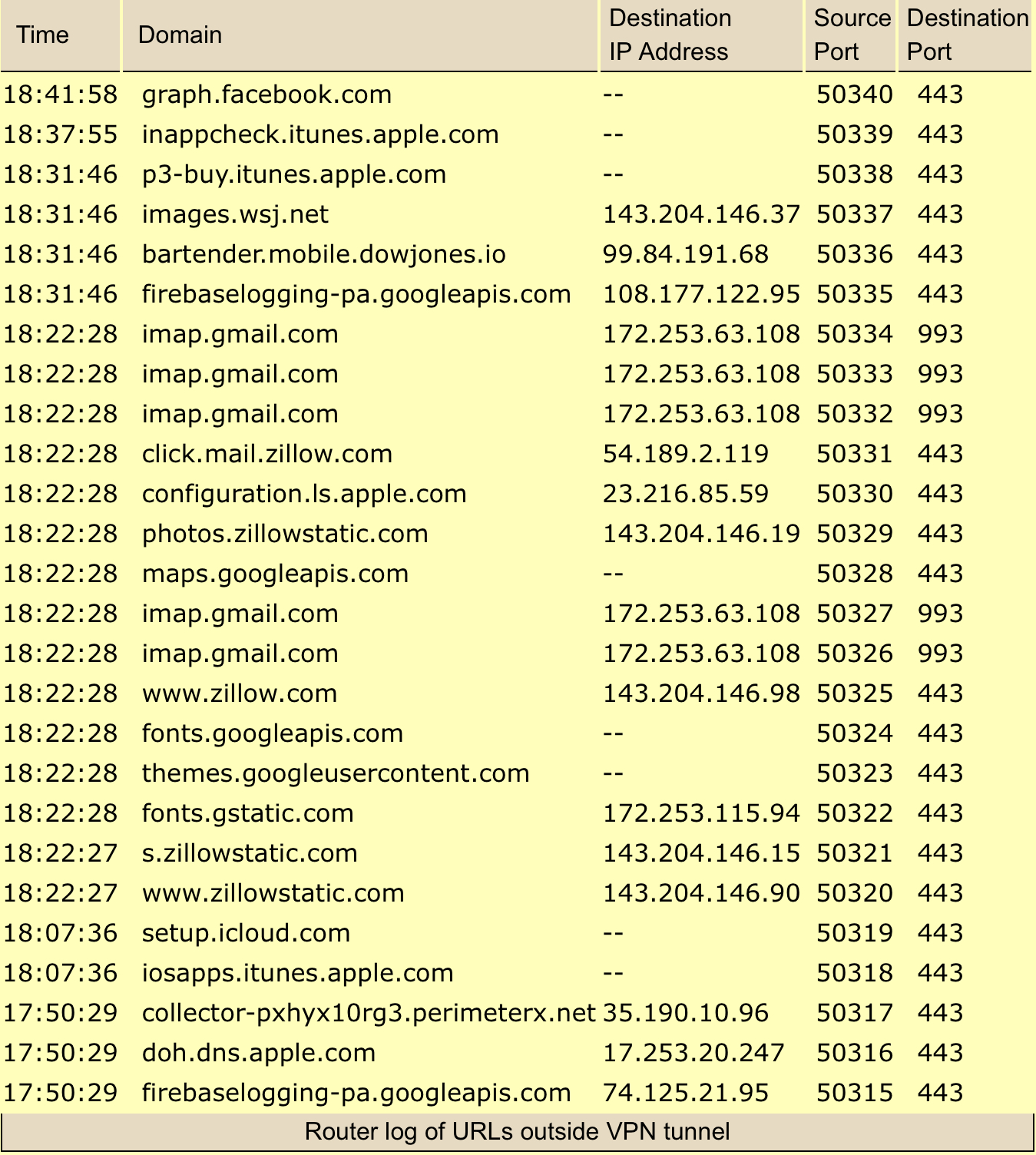
While most data does pass through the tunnel, connections made before the formation of the tunnel are still active and can (and do) transmit their own data. As Horowitz wrote, this presents a slew of problems – connections outside your VPN communicate your real IP address and are vulnerable to ISP spying. There’s also no guarantee that they are encrypted or if they provide a trustworthy DNS service.
Now, this may not seem like such a big issue if you’re only using VPNs to access Netflix content from other countries. But for the people who rely on them for work or personal safety – especially in places where surveillance and civil rights abuses are common – this flaw poses a real security risk and could literally mean the difference between life and death.
This exploit, believe it or not, isn’t new – back in 2020, VPN provider ProtonVPN had already reported the problem in its blog, saying that it goes back at least to iOS 13.3.1. More worryingly, it seems that Apple doesn’t consider this a bug, telling Horowitz that “the behaviour you are seeing is expected.” It’s no wonder, then, that months after he uncovered the vulnerability back in May, Cupertino has not moved to patch it as of the latest 15.6.1 update.
Even worse, the connections made outside of VPN tunnels are feeding data back to Apple’s own servers, including its push notification system and its own DNS service. That’s a further ding on a company that has made privacy and security its calling card, time and time again telling users it doesn’t track their movements, purchases or messages. Horowitz reported that during his testing, his iPad was even connected to Facebook, despite not having Facebook or Instagram installed.
Apple, for its part, points out that it added a “kill switch” starting in iOS 14, which supposedly routes all traffic through the VPN. Unfortunately, ProtonVPN wrote that while the functionality has blocked additional network traffic, “certain DNS queries from Apple services can still be sent from outside the VPN connection.” Horowitz says the system is also very buggy, discouraging most VPN providers from incorporating it into their services.
So, if you need to rely on your Internet connection to be secure, what can you do? Not much, really. ProtonVPN did suggest turning Airplane Mode on and off while the VPN was on to force connections outside the tunnel to be terminated. However, Horowitz said that this work around, which the company itself said cannot be guaranteed to be 100% effective, was causing issues with ProtonVPN’s own always-on function, negating its usability.
Horowitz himself suggested that you could use VPN client software on the router level, rather than on an iOS device, recommending a dedicated VPN router for this purpose. It’s a shame, however, that people would need to purchase another piece of hardware just to get a secure Internet connection – and it’s definitely not a good look on Apple.
Also, if you’re going to purchase a VPN subscription, do make sure it’s from the official website. There are fake websites selling VPN services through Facebook ads that could put your personal data at risk.
0 comments :
Post a Comment